 The web was never designed to be personal. Until Netscape added cookies to its servers and browsers in 1994 there was no way for a web server to store data on a user’s computer. In 1996 there was a bit of a ruckus in the media about the privacy implications of cookies, then everyone relaxed a bit and got used to them.
The web was never designed to be personal. Until Netscape added cookies to its servers and browsers in 1994 there was no way for a web server to store data on a user’s computer. In 1996 there was a bit of a ruckus in the media about the privacy implications of cookies, then everyone relaxed a bit and got used to them.
Fifteen years later, the European Union has leapt into action and is now keen to enforce legislation in
this area (despite a last-minute reprieve for the UK). As cookies are clearly defined and limited in scope, they make a good attack surface for legislators.
The Internet, and mobile in particular, have moved on a bit in the last 15 years, however.
Mobile apps, scattering data
I would happily predict that even in 20 years there will not be a 100% reliable, always-on, cheap wireless broadband option.
So unless you reside in Mountain View, Calif., luxuriating in virtually unlimited mobile data connectivity, I think you’re going to find living 100% on the mobile web to be a pretty miserable experience.
Conversely, it will be harder and harder to find examples of apps on mobile devices that do not benefit from connection to data networks.
So, unfortunately for the legislators, the once-clear boundary between device and service continues to blur and morph.
Software and data on iPhones and other devices are going to remain smeared across devices, the open web, and various other data services. Let’s look at how this currently works.
Unique Device Identifiers (UDIDs)
To track a user across multiple apps you’d need some way of putting a unique tag on each device so that no matter which app read it, you’d know you had the same person.
This is precisely what the Unique Device Identifier (UDID) number on iOS devices can do. It’s easily available to the writer of an app, and it cannot practically be changed or deleted.
These UDIDs allow developers to link data collected by different apps. (Interestingly, as the UDID acronym gets bandied about it will probably become irrationally feared.) Apple forbids the sharing of this data between companies, but within a company there is no effective means of preventing this.
The Shared Keychain in iOS allows apps published by a single developer to share data if they find themselves installed on the same iOS device — no network required.
Here’s a theoretical example of how this might apply to apps from an insurance company:
- You provide your date of birth to a motor insurance app to get a quick quote.
- A year later you download a pension calculator app from a different division of the same company.
- The pension app already knows your age, so it can get straight down to convincing you to buy savings products.
Data access to the Internet, with local storage on the device
The elephant in the room when talking about data protection is the fact that any app can silently connect to the Internet and send and receive data to its heart’s content.
Developers are encouraged to show a spinner to indicate that the network is being accessed, but this is a guideline rather than an enforced requirement.
This is not all about tracking users, of course. These capabilities allow things like remote throttling of app usage, enabling of new features, binding of sponsor data to parts of the app, updating media in the app, syncing with other services, etc. As there is no clear way to identify personal or tracking data within the app’s local storage, any focused privacy legislation will be tricky.
The bottom line is that your iPhone apps are increasingly likely to be using a full set of web services without you ever setting up accounts, accepting terms and conditions, logging in or even being aware of it.
Apple Push Notification Service (APNS)
One of my personal favorites in terms of potential unexpected consequences is the Apple Push Notification Service (APNS), which allows developers to remotely pop up messages on iOS devices, or add badges with numbers to the icons of their apps.
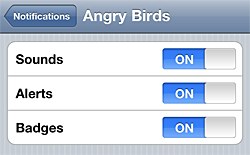 That’s all relatively straightforward, but there is also the ability to make the iPhone play any audio file included in your app, whether the app is open at the time or not. Check the push permissions for “Angry Birds” for an example (Settings > Notifications).
That’s all relatively straightforward, but there is also the ability to make the iPhone play any audio file included in your app, whether the app is open at the time or not. Check the push permissions for “Angry Birds” for an example (Settings > Notifications).
When you installed “Angry Birds,” Rovio explicitly asked for your permission to play sounds from Angry Birds on your phone whenever they like.
As an aside —
If you’re looking for true Internet notoriety, then gaining control of Rovio’s servers would allow you to remotely command all iOS devices with Angry Birds installed to “tweet” (audibly, not via Twitter) in unison.
Data handling on PCs vs. data handling on mobile apps
Given all that’s happening right now, how are we doing on transparency and consent?
Let’s compare some of the warnings and alerts you might get from three different use cases:
Case 1: Installing software on your PC that uses data on the Internet
- Warning: this software was downloaded from the Internet
- Please enter your administrator password to install
- Antivirus warning: new software identified
- Firewall warning: Unauthorized software trying to connect to the Internet
And when you run your new PC-based software:
- Please provide your email to register your account
- Please set a password
- Click the confirm link in the email we’ve sent you to authorize your account
- Accept the terms and conditions
Case 2: Accessing a website through a PC
- Please install Flash plugin / authorize Java applet / install Silverlight
- Register or log in
- Provide email address / password
- Click link in registration confirmation email
- Can I set a cookie on your PC? (Thank you, EU)
- Please accept the terms and conditions
Case 3: Installing an Internet-enabled app on your iPhone
- Tap to install app
- Errr…
- That’s it
Some final thoughts
The comparison between PC-based software and smartphone software shown above is stark, with many implications. There’s a lot to work out, and there’s a lot to debate. With that in mind, here’s a few discussion points I think are worth exploring:
- The “app way” of working could be great for business, but it only works if you trust the app delivery platform and the app developer. Organizations create and destroy trust in many ways, and we might benefit from a more explicit review of or focus on this.
- Developers could be more open about what they are doing, but explaining technical issues in plain English can be tough. Frankly, most users aren’t that interested, either.
- New laws to control use of cookies are focusing on what legislators can see and understand. Legislation will always trail technology, leading to more “privacy theater.”
- Broader technology legislation that relies on applying judgement and intelligent interpretation may succeed more than narrow, knee-jerk legislation and zero tolerance.
- The iPad brings the smartphone approach closer to the standard PC. Expect Mac OS X Lion to bring it all the way.
- Just because it fits in your pocket, doesn’t make it private.
Related:
