As any programmer knows, writing the “hello, world” program is the canonical elementary exercise in any new programming language. Getting devices to interact with the world is the foundation of the Internet of Things, and enabling devices to learn about their surroundings is the “hello world” of mobility.
On a recent trip to Washington D.C., I attended the first DC iBeacon Meetup. iBeacons are exciting. Retailers are revolutionizing shopping by applying new indoor proximity technologies and developing the physical world analog of the data that a web-based retailer like Amazon can routinely collect. A few days ago, I tweeted about an analysis of the beacon market, which noted that “[beacons] are poised to transform how retailers, event organizers, transit systems, enterprises, and educational institutions communicate with people indoors” — and could even be used in home automation systems.
I got to see the ground floor of the disruption in action at the meetup in DC, which featured presentations by a few notable local companies, including Radius Networks, the developer of the CES scavenger hunt app for iOS. When I first heard of the app, I almost bought a ticket to Las Vegas to experience the app for myself, so it was something of a cool moment to hear about the technology from the developer of an application that I’d admired from afar.
After the presentations, I had a chance to talk with David Helms of Radius. Helms was drawn to work at Radius for the same reason I was compelled to attend the iBeacon meetup. As he put it, “The first step in extending the mobile computing experience beyond the confines of that slab of glass in your pocket is when it can recognize the world around it and interact with it, and proximity is the ‘Hello’ of the Internet of Things revolution.”
For such a source of excitement in the industry, proximity is a simple protocol. Periodic “beacon” transmissions contain three numbers: (1) a UUID, which is typically used for an organizationally unique identifier, such as a company, (2) a major number, and (3) a minor number. Major and minor numbers are assigned in whatever way the organization desires to use them. A typical usage would be in a company with many stores: the major number would be used for a store number and the minor number might be used for a department or display.
With such a limited protocol, most of the exciting work happens inside an application running on your mobile device. Beacons themselves have no ability to learn about geographic coordinates like latitude/longitude or street addresses; to translate the three numbers in a beacon’s broadcast into a location, you need to pull from something else, such as a web service. They are not able to find out what else is in the neighborhood because they are transmit-only devices. It is possible to use a beacon’s broadcasts to perform “ranging,” or estimating the distance between a device and a beacon, but that is a function performed by the underlying operating system and cannot be done in a power-efficient manner.
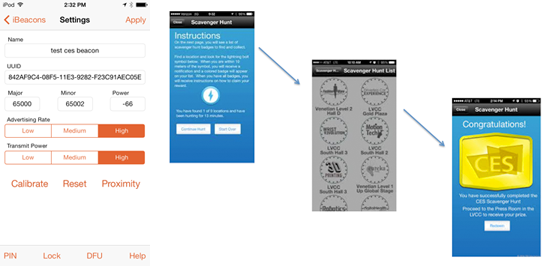
The CES scavenger hunt application is a simple listener that implements a “virtual punch card.” Nine locations on the CES show floor were equipped with beacons, and conference attendees who visited all nine locations completed a virtual card in the application and were entitled to receive a gift from the show. Each of the nine beacons had a unique signature, decoded by Alasdair Allan and Sandeep Mistry in Make magazine.
With such a simple protocol, you don’t need much to get started. Bluetooth 4.0 is the first version that supports low-energy beacons, and hardware is widely available. You can use a dedicated USB device plugged into a computer or a small computer like the Raspberry Pi, a self-contained USB device like Radius’ RadBeacon, or software running on a computing device that has the appropriate Bluetooth hardware. Radius produces a free tool for iOS called Locate for iBeacon as well as an inexpensive Mac app called MacBeacon.
Radius’ RadBeacon, attached to an Apple USB charger.
At the DC meetup, Radius was giving away RadBeacons, and I was lucky enough to win one (pictured right). It’s a tiny device. In this photo, the RadBeacon is plugged into an Apple USB charger, and you can see it dwarfed by the electronics to supply power through the USB interface.
Configuring the RadBeacon is a snap. Apple’s iBeacon specifications don’t prescribe a method of configuration, so some may be configured by their USB hosts. The RadBeacon is configured over Bluetooth. Although the iBeacon spec is transmit-only, the management can take place using two-way communications over Bluetooth.
RadBeacon’s configuration screen allows you to set the three numbers in the beacon tuple (UUID, major, and minor). Illustrated in the screen shot below, I used the article from Make to put in the beacon details from one of the beacons the CES app looks for. As a result, if you open the CES app, you’ll be virtually on the show floor in Las Vegas, and you can even earn badges. When I set up the RadBeacon in a hotel room recently, it took me about five minutes to unpack the device, get it running, and pretend to be on the floor in Las Vegas.
With everything in a beacon being totally open to anybody with a receiver, security is not a strong suit of the protocol. (If you want to investigate your Bluetooth neighborhood, download and install the free LightBlue app from the iOS app store.) As David Helms noted, the security model is “essentially worthless,” and he advocated that developers “design solutions on the assumption that the beacon information is accessible to third parties.” Defensive tactics depend on the value of the information in the app; for the CES scavenger hunt, Radius didn’t implement extensive security measures, Helms explained, but instead they used “an audit trail that validated the game progress of the players based on time and location to ensure reasonably fair game play, which was a cost-effective strategy to meet the goal.” With more at stake, Helms said, developers might need to include more sophisticated security mechanisms to address the potential for interception, spoofing, and the limited ability to ensure that a client device can be a trusted computing platform.
Although the technology of iBeacon is not complex, incorporating proximity into existing or new applications may be a challenge. In the past decade, I’ve seen many organizations try to use Wi-Fi for proximity, which is at best a rough guess. Helms pointed out that more accurate location information based on beacons allows application developers to “design amazing experiences for their customers and users by drawing on deep knowledge of their particular market.”
Of the many things I’ve learned from O’Reilly, one of the most important is to follow the developers. I started learning about BLE and beacons because of the excitement and exchange of ideas. In our conversation, David confessed to being “blown away with the amazing new ideas and projects using proximity and iBeacons that thousands of developers are building every day.” I am totally with him on that point, and I’ll be returning to the use of proximity information in application development as I continue to learn more.