
OpenID, the lightweight, decentralized identity system (Radar post) had an interesting weekend. There is now a method for using your Yahoo ID with OpenID (unofficial, but sanctioned) and there are new measures designed to reduce the risk of phishing.
First, ex-Yahoo Simon Willison has created a proxy to allow you to use your Yahoo Id as an OpenID.
idproxy.net, launched today, is my attempt at speeding up the process. It uses Yahoo!’s Browser-Based Authentication API to allow you to sign in with a Yahoo! account, then lets you create one or more OpenIDs (of the form something.idproxy.net) to use with sites that support the OpenID standard.
In effect, it lets you use your Yahoo! account as an OpenID.
Click thru for more..
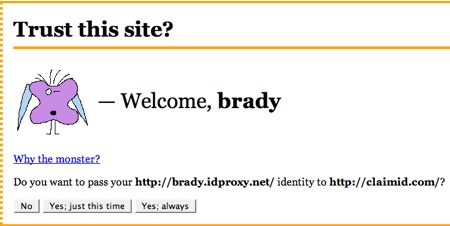
I’ve used it. It works (as seen in the image above). It took me all of 30 seconds to create an OpenID via Simon’s server. Yahoo! as you can see below allows you disable the connection quite easily and does a good, non-scary job of explaining what you are doing when you press the “Allow” button. From the Yahoo! page:
Now we need your permission!
In order to use http://idproxy.net, you need to give us permission that http://idproxy.net may recognize you once you return to this application.
Keep in mind:
* http://idproxy.net will not be able to access any data you keep on Yahoo! other than the data identified above.
* The permission will expire in 2 weeks.
* You can change this permission by visiting Account Info and selecting the Partner Accounts link. Note that revoking permission may take up to 24 hours.
* If you change your password, you may be required to give permission again.
* Yahoo! has no affiliation with http://idproxy.net and cannot guarantee the security of any user data that you permit http://idproxy.net to access.
For further reading also check out Sam Sethi’s thoughts on this topic; based on his tip I am going to try Sxip‘s new Firefox plugin Sxipper to manage my various OpenIDs – I’ll report back later. [Found via Techmeme and currently on Digg]
Second, it’s notable the OpenID developer community has responded to the phishing concerns. If you are not aware, phishing is when a malicious website pretends to be another website (GMail, Yahoo!, MySpace) in order to get your login information (protect yourself, learn more). When logging in to a site with OpenID you are redirected away form that original site to your OpenID provider — this is a prime place for a phishing site to harvest your credentials. Because of these concerns it was great to see Scott Kveton posting that MyOpenID, an OpenID provider, is implementing two methods to try to combat phishing. From his post:
- Personal Icon: A Personal Icon is a picture that you can specify that is presented to you in the title bar of MyOpenID every time you visit the site. The image is shown based on a cookie that is not tied to your account. This aids in fighting phishing as you’ll get used to seeing the same picture at the top of the page every time you sign in. If you don’t see it, then something might be up. Carl worked on this feature for us over the last few days and it employs several of the techniques discussed on the list to make it happen. You can see the picture next to this text that shows my Personal Icon which is a picture of my son Živio in the bathtub.
- SafeSignIn: The SafeSignIn feature was inspired by Simon Willison and was implemented by Mike on our Identity Provider team. SafeSignIn is an option that users can set on their settings page that makes it so you cannot be redirected to your MyOpenID.com to enter a password. If you are redirected to MyOpenID.com from another site, you are presented with the dialog you see below prompting you to either use a bookmark or enter the address in your location bar in the browser. This is an optional feature but we highly recommend you enable it.
Simon Willison has implemented similar measures for idproxy.net (he uses MonsterID for the personal icon).
Working on phishing and unofficial support by another large company (Six Apart is a major backer) will hopefully get some more mainstream movement happening in this space. As our previous post noted, OpenID is on the upswing, but it still needs to gain acceptance at more, larger sites. I think it is safe bet that Yahoo! will be the next member of the Alexa 100 to implement OpenID.
Kaliya Hamlin, Identity Woman, will be doing a session on User-centric Identity Systems (including OpenID) and David Recordon (Verisign) will give a session on Implementing OpenID at the Web 2.0 Expo this April. Simon Willison will also be speaking.
