Update, 4/27/11 — Apple has posted a response to questions raised in this report and others.
By Alasdair Allan and Pete Warden
 I don’t think either of us were expecting to see this story strike such a nerve. There’s been some amazing detective work from researchers across the web, and so here’s a selection of the most interesting immediate reactions.
I don’t think either of us were expecting to see this story strike such a nerve. There’s been some amazing detective work from researchers across the web, and so here’s a selection of the most interesting immediate reactions.
Alex Levinson — Right from launch, we had an FAQ pointing to articles by people like Ryan Neal and Paul Courbis who had found this file (consolidated.db) before, but hadn’t understood or been able to communicate its significance. The main reason we went public with this was exactly because it already seemed to be an open secret among people who make their living doing forensic phone analysis, but not among the general public — even pretty geeky people like Alasdair and me. We were freaked out by the implications of this data and how unprotected it was, but most of the forensics community seemed to miss quite how creepy ordinary people would find it.
I do appreciate how frustrating this must be for Alex though, and would like to apologize personally to him that we didn’t include his article among the prior research we cited. Unlike the others, it didn’t show up in web searches or the books we referenced. It also didn’t help that most of the follow-up articles by other people left out the details that we’d tried to make clear about who found it first. We obviously didn’t communicate it as well as we thought we had, which is completely our fault.
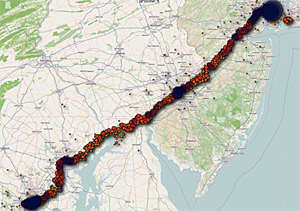
My Life According to the iPhone’s Secret Tracking Log — Alexis Madrigal has a far more interesting life than me, judging by his map. I especially like the points from a flight with Jim Fallows somewhere over West Virginia. As he says, this data can be incredibly interesting, and as data geeks we were just as fascinated as he is. I actually look forward to a future where we can use this sort of information, but with the user’s permission.
Apple is not “recording your moves” — Both of us have been following Will Clarke’s blog for a while and we liked this article. It’s good to look skeptically at the accuracy of the data both in space and time. We do disagree about one of the conclusions though: that the points are just the locations of cell towers. That was one of our first thoughts when we saw the data. But the fact that there’s thousands of different points scattered across small areas, all in slightly different places, seems like pretty strong evidence that they’re not just the locations of cell towers. Another way of putting that is that there’s a lot more points than there are towers. There’s also lots of points with the same tower ID code that are in different locations. That all led to our conclusion that it was trying to figure out the device’s position, even if it wasn’t very good at it.
Until we get a deeper analysis, that’s just a provisional conclusion of course. But getting smart folks like Will to dig into this and correct anything we’ve got wrong is exactly why we open-sourced it. He also picks up on the Las Vegas Anomaly. Multiple people have reported seeing a phantom trip to the city show up, and one theory (other than a lot of lost weekends) is that Apple has an unpacking or testing facility there. Alasdair’s phone that was shipped with iOS4 shows this, whereas my older device that originally had iOS3 doesn’t, which was suggestive. I wonder if Will’s device is a newer one, too?
OpenStreetMap — The application we released relies on this volunteer-run site to render the background map tiles. We ended up tripling their usual load, according to a team member. They actually fired up extra servers to cope, so I made sure to add a link to their donation page from our main site. If you got something out of the application, please do consider giving something to them, or even getting involved. It’s a fantastic team and community. How many other organizations would have responded to heavy usage by a free client by paying for more servers themselves? I even messed up their credit text on the initial version of the application, but they were very understanding about that too.
Related:
